Today penetration testing (pen testing) is one of the most important investments that you can make to protect your network.
The Problem: External Intrusion and Penetration
External intrusion and penetration is one of the silent stalkers on the Internet. External hackers can penetrate your network and not leave a trace that indicates they have stolen your intellectual property or private information. In fact, they can render your computers and network completely useless without your knowledge.
Penetration from the outside can result in loss of intellectual property, identity theft, and data theft to loss of network control. Sadly, the way the laws are written make your company responsible for damages resulting from these security breaches.
Statistically there is a very good chance that your outward-facing IP addresses are being scanned right now and are secretly susceptible to unwanted penetration. You may be the low-hanging fruit that they are looking for.
There are thousands of methods that hackers use to penetrate your network, including DDOS attacks, SYN-FIN attacks, Port 0 attacks, SQL injections, Heartbleed attacks, and forbidden site attacks…the list goes on and on.
The Solution: Oasis Technology Vulnerability Analysis
Oasis Technology will run extensive vulnerability analysis on your outward-facing IP addresses to determine what weaknesses exist and what routes external hackers can use to obtain access to your computers, networks, and data.
- This analysis is non-invasive and we do not have to be onsite to perform the tests.
- A component of this analysis includes PCI compliance testing to also ensure that your network is PCI compliant.
- We will provide you with hard copy reports listing all security weaknesses.
Oasis Technology’s analysis will pin-point all external weaknesses that exist for your outward-facing network. If we locate any weaknesses, we can recommend solutions to close your security holes.
We know this is important to you — call us and we will get back you to immediately with a quote to perform your comprehensive penetration testing and review.
Make sure your organization doesn’t get hacked or pre-attacked! Contact Oasis Technology today. We are here to ensure that your data, systems, and entire network are secure.
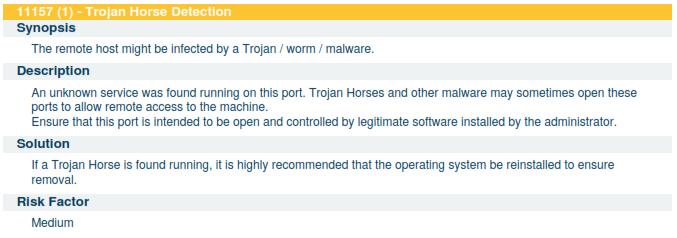
Below is an example of a vulnerability found in one of our actual scans.